
About Us
About Arka7
At Arka7, we are on a mission to secure the digital future. In an age where data breaches, cyberattacks, and digital threats are becoming increasingly sophisticated, we believe that everyone deserves the right to be protected online. That's why we've dedicated ourselves to delivering cutting-edge cybersecurity solutions that empower individuals and businesses to defend against the evolving landscape of cyber threats.
Our Vision
Our vision is a world where digital security is a fundamental right, not a luxury. We envision a landscape where individuals can browse the internet, make online transactions, and communicate freely without fear of cyberattacks. We strive to build a digital environment where businesses can thrive, innovate, and grow securely, knowing that their digital assets and customer data are safeguarded.
Our Mission
Our mission is to provide the most advanced and accessible cybersecurity solutions that protect individuals, organizations, and communities from cyber threats. We are committed to staying at the forefront of cybersecurity technology, continuously adapting to emerging threats, and educating our clients to make informed decisions about their digital security.
Our Services
Our services combine manual and automated testing to identify both technical & business logic issues while delivering in-depth reports with step-by-step POCs, detailed fix information and secure code examples.
Penetration testing
Our highly skilled team conducts meticulous and rigorous penetration testing to assess your system's vulnerabilities. We simulate real-world attacks to identify weaknesses and provide actionable recommendations to fortify your defenses.
Vulnerability Assessment
We perform thorough vulnerability assessments to identify potential security loopholes within your networks, applications, and infrastructure. Through automated scans and manual analysis, we help you understand the risks and prioritize remediation efforts.
Security Audits
Our comprehensive security audits evaluate your organization's adherence to industry best practices and compliance standards. We assess your security policies, procedures, and controls, providing insights to enhance your overall security posture
Cloud Security
Our cloud security services include cloud infrastructure, applications and corporate network interaction for IaaS, PaaS & SaaS
Social Engineering
We employ ethical social engineering techniques to assess your employees' susceptibility to various manipulation techniques such as phishing, impersonation, or physical intrusion. Our training programs help educate your workforce and create a resilient security culture.
Compliance Advisory
Our team assists in developing robust incident response plans to minimize the impact of potential cyber incidents. We help you define escalation procedures, establish communication protocols, and provide guidance throughout the incident response process.
Why choose us?
In a digital landscape fraught with ever-evolving threats and vulnerabilities, the choice of your cybersecurity partner is crucial. At Arka7, we stand out from the crowd for a multitude of compelling reasons:

Flexible and customizable services
Services are re-engineered and re-designed to meet the custom needs of the customer.
Skilled consultants
Consultants with niche skills and industry accepted certifications are on-boarded in the team to ensure quality deliverables.
Best industry solutions
Industry trusted and effective solutions are selected and configured to suit customers expectations.
Call To Action
Choosing the right cybersecurity partner can make all the difference in protecting your digital assets and maintaining your peace of mind. At Arka7, we're not just a choice; we're the right choice. Join us in the fight for digital security, and let's build a safer digital future together.

What Sets Us Apart?
-
Expertise
Our team consists of certified professionals with extensive experience in cybersecurity. We keep up with the latest threats, vulnerabilities, and industry best practices to provide you with cutting-edge solutions.
-
Tailored Approach
We understand that every organization has unique cybersecurity requirements. We tailor our services to your specific needs, ensuring that you receive customized and effective solutions.
-
Proven Track Record
We have a strong track record of successfully helping organizations across various industries strengthen their cybersecurity posture. Our client testimonials speak to our commitment to excellence.
-
Confidentiality
We prioritize the confidentiality of our clients' information. Our stringent security protocols ensure that your data remains secure throughout our engagement.
Our Approach
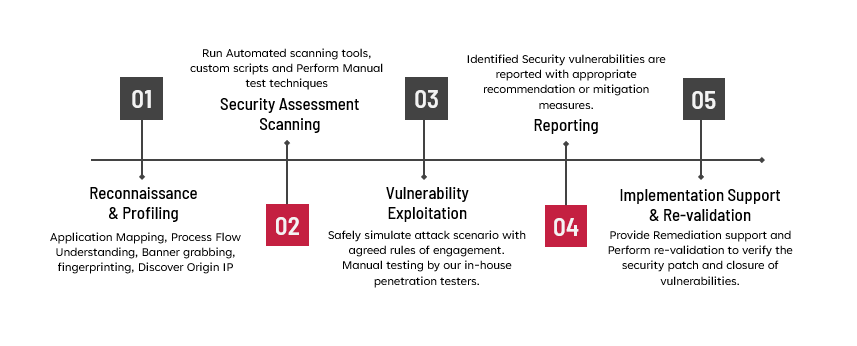
Frequently Asked Questions
Here are the answers to the most commonly asked questions
-
What is cybersecurity, and why is it important?
Cybersecurity is the practice of protecting digital systems, networks, and data from unauthorized access, attacks, and damage. It's crucial because it safeguards sensitive information, prevents financial losses, and maintains the trust of clients and customers.
-
What are common cybersecurity threats?
Common threats include malware (e.g., viruses and ransomware), phishing attacks, DDoS attacks, data breaches, and insider threats.
-
How can your cybersecurity firm help protect my business?
We provide a range of services such as threat detection, vulnerability assessment, security awareness training, and incident response to identify, prevent, and mitigate cybersecurity risks.
-
What industries do you serve?
We serve a wide range of industries, including healthcare, finance, e-commerce, manufacturing, government, and more. Our solutions are tailored to meet the unique security needs of each industry.
-
What is a vulnerability assessment, and why do I need one?
A vulnerability assessment is a systematic review of your network and systems to identify weaknesses that could be exploited by cyber attackers. It's essential to proactively address security gaps before they are compromised.
-
How does your threat detection system work?
Our threat detection system uses advanced algorithms and real-time monitoring to identify unusual activities, known malware signatures, and emerging threats. It alerts our security team, allowing us to respond swiftly.
-
How can I get started with your cybersecurity services?
Contact us via phone or email, and our team will schedule a consultation to assess your specific needs and develop a tailored cybersecurity plan.

